Information Security Consulting
Need help securing your technology? Want to know where the gaps are in your security plan? We offer security architecture review and gap analysis. We can create, implement and maintain your security architecture for a wide variety of environments and business models.
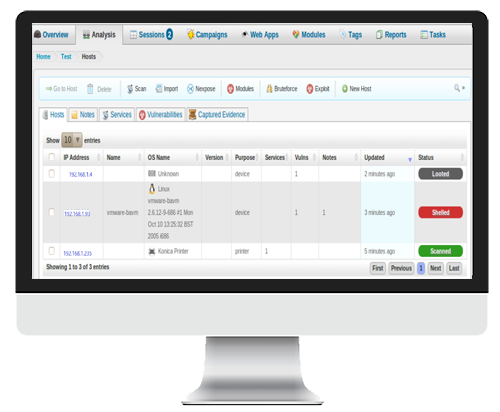
Vulnerability Assessment:
Internal (what only you should see)
Network
Application
Website
Physical
External (what the public can see)
Website
Unintended Exposures
We provide concise reporting of all findings.
We recommend realistic mitigation options and real solutions.
Policy:
Evaluate existing company policies
Recommend best business practice tailored to your organization


PCI Assessment:
Evaluate your existing configuration for taking payments
Provide optional solutions and recommendations
Assist in preparation for PCI audits
Security Architecture Review
Evaluate your existing infrastructure and conduct gap analysis
Provide options and solution based on best practice and budget
Provide implementation or advise during implementation
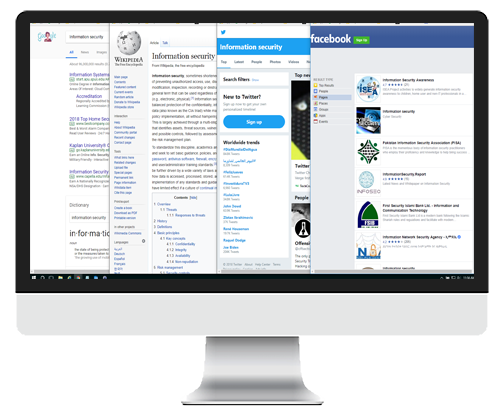
Sensitive or Personal Information Search for Company and Executives
Find what information is available on the internet about your company, managers and employees
Find public postings about your company
Make recommendations
Physical Security Check
Cameras/CCTV
Fencing
Doors/Locks
Visitor access control


Application Review
Utilizing OWASP methodology
Business Continuity, Disaster Response and Recovery Plan Review
Identify critical systems or business functions
Prioritize replacement/recovery items
Plan and evaluate backup and recovery options
Penetration Testing
Test and validate security defense levels
Network
Application
Website
Physical
Cloud
Social Engineering
We provide concise reporting of all findings.
We recommend realistic mitigation options and real solutions.
Internet of Things (IOT):
Security assessment
Securing and risk mitigation
Training Tailored to your Business for Systems and Security:
Hardware
Operating System
Application
Security practices
