Network Isolation
Network Isolation and the benefits of implementing a DMZ
Due to the interchangeability of terminology used in this article, the word “server” will be referring to the physical or virtual hardware and the operating system which is hosts. Whereas the word “service” will refer to any additional software which serves a dedicated role in the network.
At some point, every network engineer encounters a situation where they need finer control over the network accessibility of the servers that they are responsible for. This additional control is often used for configuring remote management and for preventing unauthorized access. To this end, implementing a firewall is often the preferred solution.
A typical firewall is a rule-based state engine which allows for the denial, processing, manipulation, and forwarding of network traffic. Most firewalls are implemented on the OS level, as they need to be capable of direct control over the server’s network interfaces. In the rest of this article, we will be covering how firewalls can be used for network isolation, and how to leverage them for the creation of a DMZ.
Network isolation is the process of isolating servers or entire machines from parts of your network. This can be accomplished by installing and configuring a firewall on each server you wish to isolate. You can individually set each firewall to only allow particular traffic from specific interfaces, specific computers, or even specific protocols.
Firewalls can be extremely powerful and versatile tools for network isolation once you learn how to use them. However, every additional firewall you install will add to the complexity of a network. This not only adds to the workload required for managing the network, but it also provides more opportunity for errors. The alternative is to use a single firewall to manage the network traffic of multiple servers. You can find an example of this by looking at most ISP provided routers. The vast majority provide a firewall which by default denies most incoming connections from the internet to help protect their client’s networks.
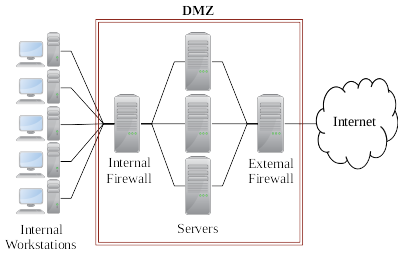
A single outward facing firewall is an excellent way to control access to multiple servers from outside the network. But threats don’t always come from outside your network, they can come from inside as-well. As such many network engineers will implement an additional firewall to limit connections to and from the internal network and between each of the servers. When you have a firewall, both externally facing and internally facing, we call this a network DMZ.
The advantages of a DMZ are substantial. Not only does a DMZ allow for easier management, as you only have two firewalls to configure, it also allows for you to control network traffic for server’s and computers which might not be capable of hosting a firewall themselves, such as IOT devices and other proprietary hardware. The primary limitations of a DMZ are caused by the processing power required to handle firewall operations and the maximum throughput for the network interfaces on each server. For a small network, this likely won’t become an issue. But the larger a network becomes and the more traffic the firewalls have to handle, the closer each firewall will get to the limits of its hardware. As such it may be prudent to implement several separate DMZs for any network of substantial size, or to provide several firewalls at each edge of a single DMZ and load balance them accordingly.
DMZs do not always require two servers each with their own distinct firewall, as you can use one server with multiple network interfaces to achieve the same effect. But the example below will show a DMZ which uses two distinct firewalls, for educational purposes.